When the AWS European Sovereign Cloud (ESC) was announced, the promise was clear: the full power of AWS, completely partitioned and resident within the European Union. For sectors like law, healthcare, and critical infrastructure, this wasn't just another region. It was the answer to strict compliance requirements that prevented cloud adoption for years.
At move2edge, we don’t just read the press releases; we build. Recently, we designed a fully sovereign platform for a client with zero tolerance for data residency risks. We expected a challenge, but the reality of this frontier environment pushed us to find unconventional solutions in cloud engineering.
Here is what we learned from the trenches of the aws.eu domain.
The "Day 1" reality check
We went in expecting an experience similar to the standard Frankfurt region, just with a better legal framework. We were wrong. The Sovereign Cloud (aws-eusc) is physically and logically separated from the global AWS ecosystem. While this isolation is its greatest security feature, it creates immediate hurdles for deployment speed.
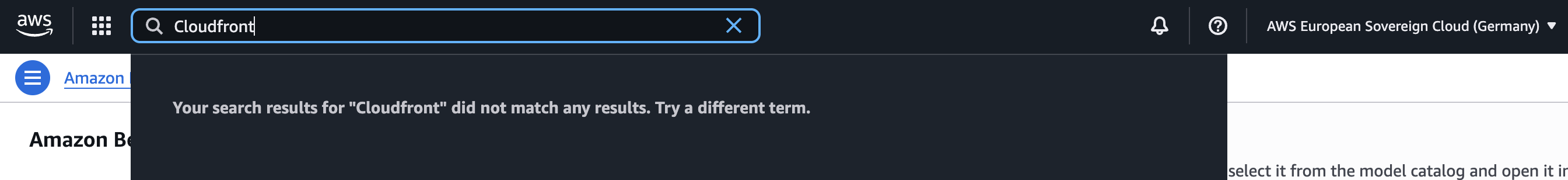
The biggest shock was the absence of edge locations. Because there is no Amazon CloudFront, traffic cannot be cached close to the user; everything must travel via the public internet directly to the single point of presence in Brandenburg.
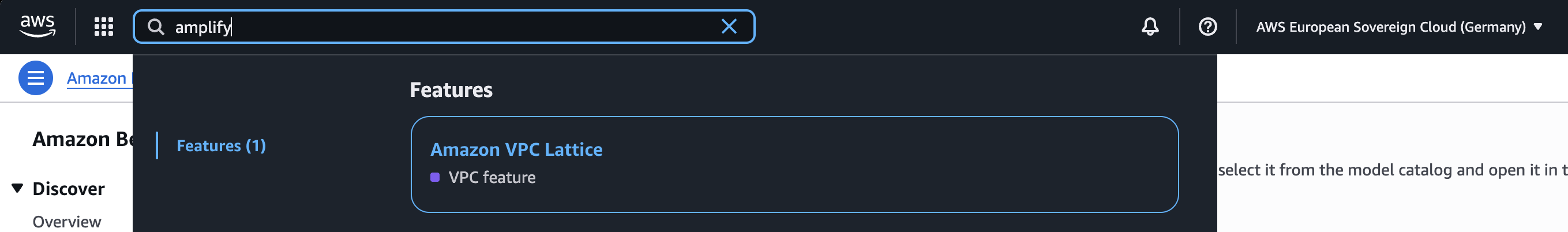
This creates a ripple effect on the developer experience. AWS Amplify simply doesn't exist here. The standard "git push" workflow for Next.js is gone. Without a CDN, the standard architecture for static hosting breaks. We had to move away from simple S3 hosting and instead containerize the application, running it on ECS behind Application Load Balancers. It’s a much heavier architecture for what should be a lightweight workload.
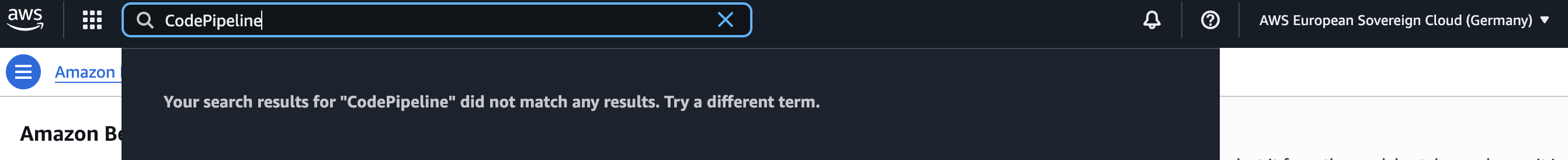
We faced similar friction with CI/CD and Infrastructure as Code. The entire AWS CodeSuite is currently unavailable, forcing us to design secure, self-hosted build pipelines to ensure artifacts never leave the sovereign environment. Even Terraform required custom configurations to correctly recognize the unique eusc-de-east-1 endpoints.
Sovereignty vs. AI capabilities
We anticipated limitations regarding language models. These constraints stem largely from licensing and legal issues. Providers like Anthropic or Meta would need to agree to deploy their model weights in an infrastructure where their US-based engineers have zero access.
As a result, Amazon Bedrock offers a very limited selection, specifically the Amazon Nova models. While we are spoiled for choice with Claude or Llama in the regular cloud, the options in ESC are restricted.
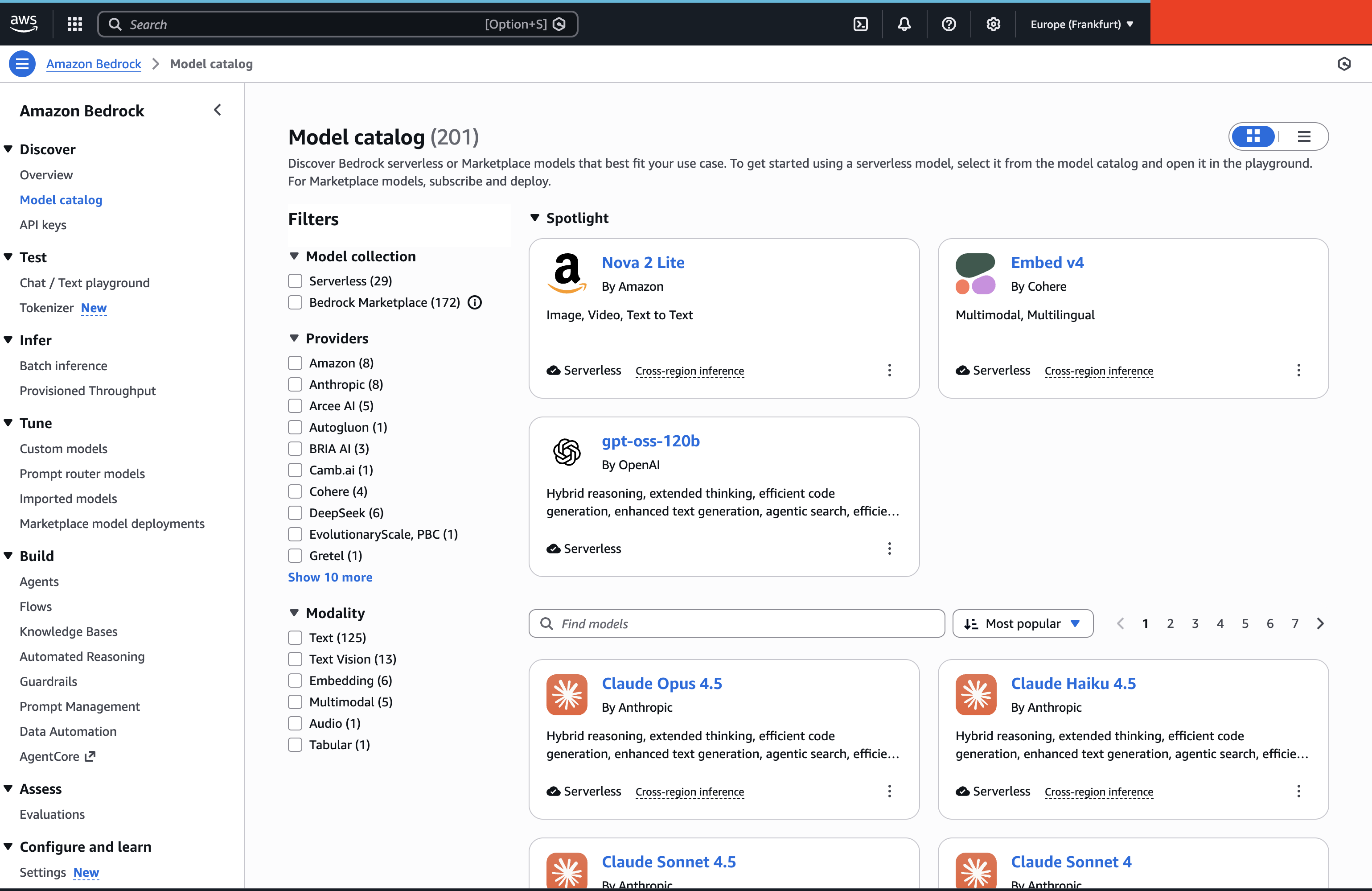
We decided not to wait. Instead of settling for the available managed models, we pivoted to a self-hosted strategy and deployed Bielik AI – a robust, Polish-language open model. By setting up a local GPU instance and networking it securely to AWS EU, we provided high-quality Polish language processing while maintaining total sovereignty. Not a single token ever left the European Union.
The hidden price tag: infrastructure vs. engineering
Beyond the missing services, there is a financial reality that every CTO must accept. There is a literal "Sovereignty Premium" - expect infrastructure costs to be roughly 15-20% higher than the Frankfurt region, with all billing handled in EUR.
However, the real cost isn't on the monthly bill; it is in engineering hours.
The launch of ESC currently forces a shift in how we build. While the core ecosystem is functional and we successfully deployed serverless functions like Lambda, the environment is not yet at parity with global regions. In many cases, European sovereign engineers must return to fundamentals: container orchestration, custom networking, and manual configuration.
AWS will undoubtedly fill these gaps over time. However, the cloud giant is known for keeping roadmaps close to the chest, rarely sharing specific release dates for new services. Until that parity is reached, building capabilities that are usually "out of the box" will simply take more time. The necessity to manually configure what is usually automated shifts the project cost structure from buying services to paying for development time.
A pragmatic breakthrough
It is worth remembering that despite the isolation, aws.eu still traces its lineage to Seattle. While purists might argue it isn’t a homegrown European hyperscaler, from an engineering and compliance perspective, this is the pragmatic breakthrough we needed. It bridges the gap between regulatory rigidity and technological maturity. We aren't forced to migrate to obscure, unproven local providers; we get to use the same battle-tested primitives that power the global internet - proven across millions of deployments - now wrapped in the legal and technical armor required by the EU.
This experience solidified our philosophy: security and compliance are not up for debate. Is containerizing simple sites a hassle? Yes. Is managing your own LLM slower? Absolutely. But for clients in critical sectors, this is the price of absolute certainty that data is immune to extraterritorial jurisdiction.
Navigating the new reality
We believe that the intersection of Sovereign AI and compliance is a niche entering a phase of hyper-growth. This project demonstrated that while the constraints of a sovereign environment are real, they are not impossible to overcome for teams with the right technical depth.
At move2edge, we have focused on building the specific competencies required for these environments from navigating missing native services to deploying private LLMs in locked-down networks. We see ourselves as partners for organizations that need to turn these regulatory constraints into architectural fortresses.
Our approach is proven. The move2edge team won the European Critical Infrastructure Hackathon 2026 by building a 'Sovereign Edition' of ZeroMissed.ai from scratch. We have demonstrated that cutting-edge AI can be built for critical infrastructure without compromising on digital independence.
The AWS European Sovereign Cloud is just the beginning. If your organization is ready to move critical workloads to a truly sovereign environment, we have already mapped the territory.






![[103] Securing Your Terraform Serverless API with Cognito](https://cdn.prod.website-files.com/67362585a7df1c57acedee7a/67600b4f8195ac0a3e9ee894_y804x.jpg)
![[102] Enhancing Your AWS Serverless API with DynamoDB for Data Persistence](https://cdn.prod.website-files.com/67362585a7df1c57acedee7a/674885347f7f6790dc367ea7_toast-on-the-floor.jpg)
![[101] Launch Your Own Secure Serverless API on AWS with Terraform](https://cdn.prod.website-files.com/67362585a7df1c57acedee7a/67371f0afb60a80f2b2c2a70_terraforming.jpg)








